Achieve Service Connection With Secure Cloud Storage Space Services
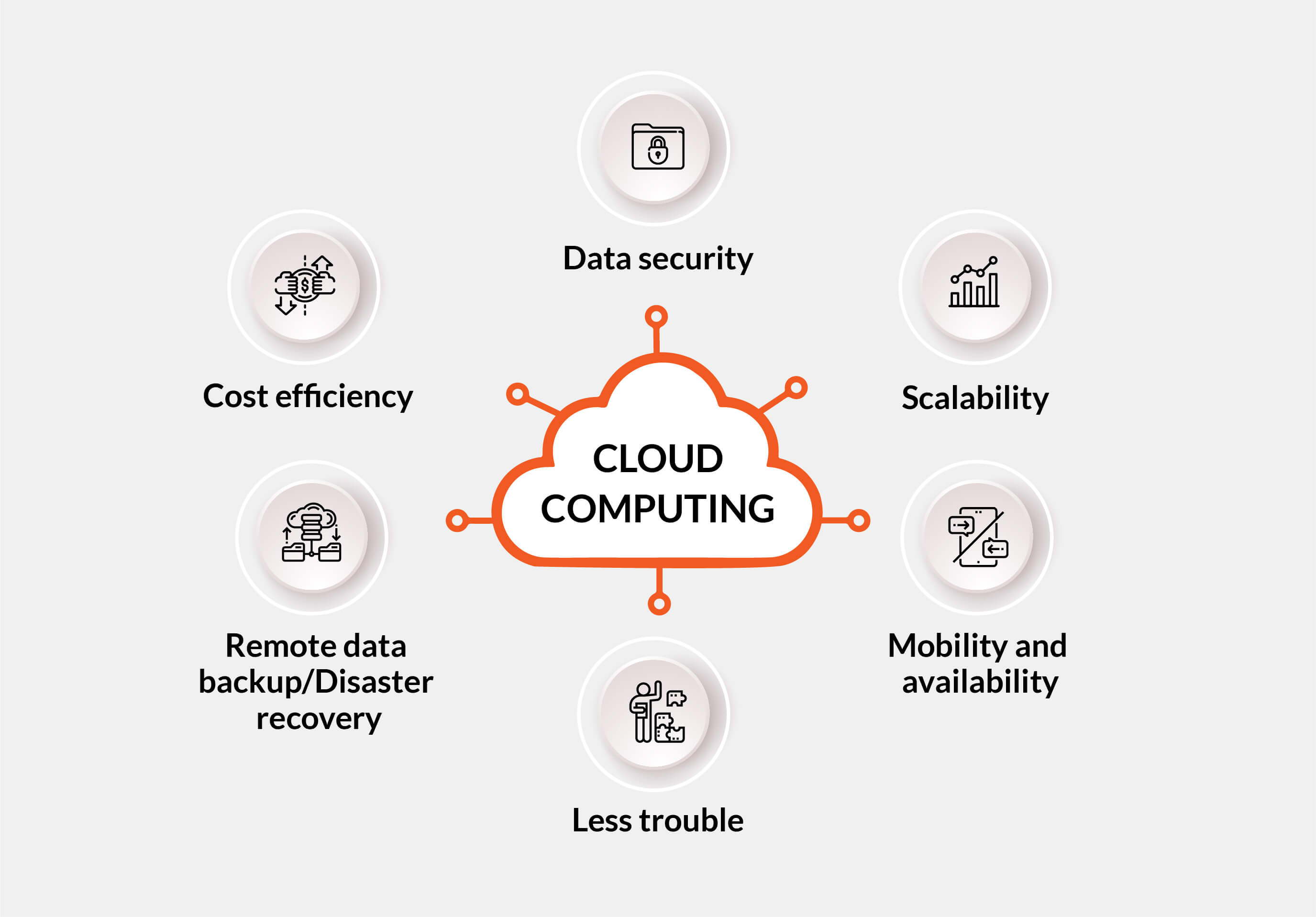
Advantages of Secure Cloud Storage Space
Undoubtedly, protected cloud storage provides organizations a wide variety of advantages in terms of data protection and ease of access. By storing information on respectable cloud platforms that employ encryption and sophisticated security actions, organizations can secure their info from unauthorized gain access to or cyber hazards. On the whole, the advantages of protected cloud storage equate into boosted information monitoring, boosted operational effectiveness, and enhanced security for businesses of all sizes.
Trick Functions for Service Connection

Additionally, one more key attribute for business continuity is redundancy. Redundancy entails having several copies of information kept in various locations to avoid a solitary factor of failing (linkdaddy cloud services press release). By distributing information throughout different servers or information facilities, services can reduce the danger of data loss and guarantee constant accessibility to their information. Overall, these vital functions function together to develop a detailed business continuity strategy that safeguards important data and operations.
Importance of Data Encryption
In today's interconnected digital landscape, securing sensitive info is vital, making the significance of data file encryption an essential aspect of preserving data integrity and protection. Information file encryption entails inscribing details as if just authorized events can access and decode it. By transforming information right into a safe and secure layout, encryption functions as a guard against unauthorized access, minimizing the risk of information breaches and cyber dangers.

Disaster Recuperation Techniques
Reliable catastrophe healing approaches are important for services to minimize prospective interruptions and make sure connection when faced with unexpected occasions. A durable calamity recovery plan entails outlining treatments to recover information, applications, and IT infrastructure in the event of a calamity. One key aspect of an efficient technique is normal information back-ups. By keeping data in safe and secure cloud storage space solutions, businesses can ensure that vital details is protected and easily available in case of a calamity. Testing the disaster recovery plan frequently is also essential to identify any kind of weaknesses and make necessary improvements. Additionally, having a marked team in charge of performing the recovery strategy can simplify the process and minimize downtime. It is necessary to take into consideration various disaster scenarios and customize the healing techniques to deal with details risks that the business may encounter. By executing detailed catastrophe recovery approaches, companies can improve their durability and protect their operations against unanticipated occasions.
Picking the Right Provider
To ensure seamless Get the facts organization continuity and reliable catastrophe healing, selecting a dependable and suitable provider for safe cloud storage is critical. When picking a cloud storage space provider, several crucial elements must be thought about. First and leading, evaluate the copyright's security steps. Guarantee they utilize durable security techniques, have strict access This Site controls, and adhere to market guidelines to secure your information. Additionally, analyze the provider's information recovery capabilities. A reputable provider should supply regular back-ups, redundancy steps, and efficient recuperation procedures to reduce downtime in situation of a catastrophe.
Your company demands might advance over time, so it's important to choose a provider that can accommodate your expanding storage space needs and adjust to transforming scenarios. By meticulously assessing these variables, you can select a cloud storage service copyright that lines up with your business's needs and makes certain constant procedures in the face of potential disruptions.
Verdict
To conclude, protected cloud storage space services use crucial benefits for attaining company connection, including enhanced safety and security functions, smooth scalability, reliable cooperation tools, durable data back-up systems, and disaster recuperation methods. Data file encryption plays an essential duty in safeguarding sensitive details, while picking the right provider is key to making sure compliance with laws and maintaining operational effectiveness. linkdaddy cloud services. Protected cloud storage space is a valuable possession in today's electronic landscape for making certain visite site uninterrupted business operations
Data backup mechanisms are critical for shielding versus data loss due to system failings, cyber-attacks, or human mistakes. By distributing data across different servers or data centers, companies can alleviate the threat of information loss and ensure continuous accessibility to their details.In today's interconnected electronic landscape, guarding delicate details is vital, making the relevance of data file encryption a basic facet of preserving information honesty and safety. By transforming information into a safe style, encryption acts as a shield against unapproved gain access to, decreasing the threat of information breaches and cyber threats.
Conformity demands and information defense laws typically mandate the usage of encryption to guard sensitive details, stressing its vital duty in modern information security strategies.